How to bump node packages specially when there are security vulnerabilities
September 07, 2019
Upgrading packages, for the good sake of keeping them upto-date or for the reason one or few packages has security vulnerabilities, quite often easier! But sometimes it gets tricky and bite us. However auditing and understanding how the packages are used by other packages give us clear picture.
Tools you required: yarn and npm-check-updates
To install npm-check-updates,
run yarn global add npm-check-updates. it will create alias ncu
Strategy for upgrading particular package/particular group of packages (suitable for projects with lot of dependencies or for projects with less test coverage):
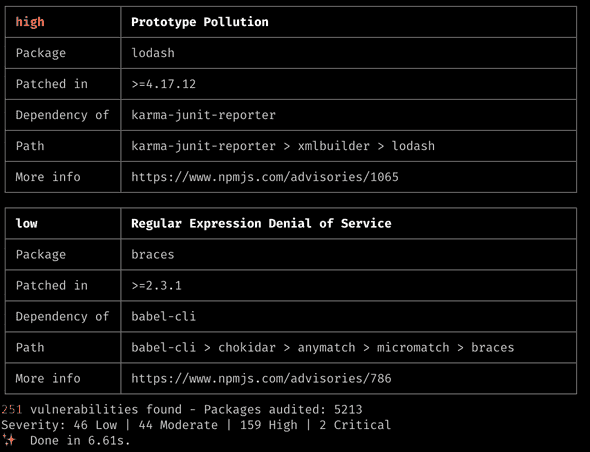
Fig.1. yarn audit
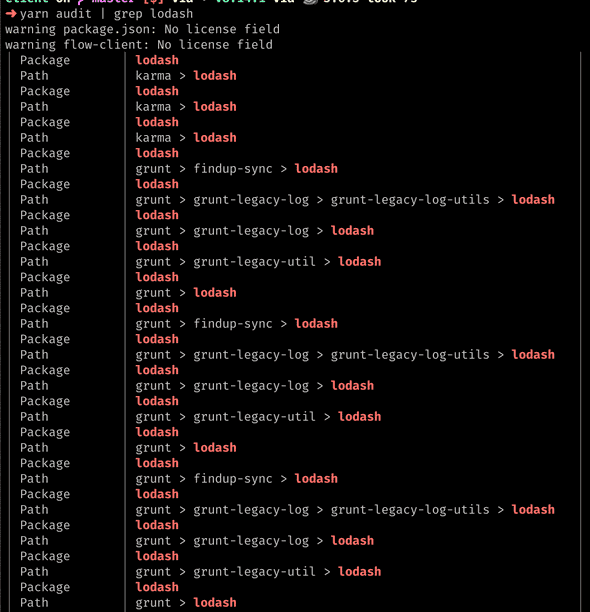
Fig.2. yarn audit | grep lodash
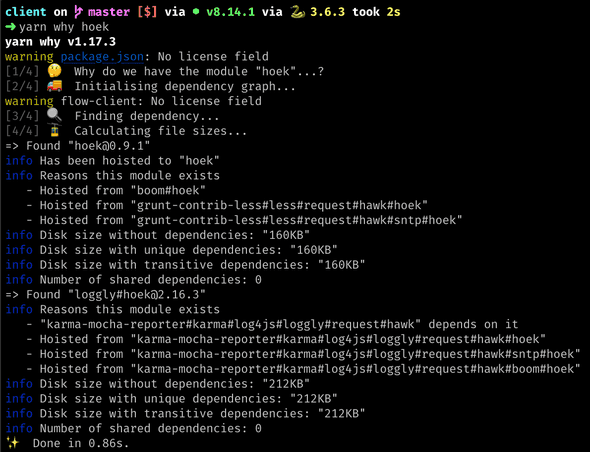
Fig.3. yarn why hoek
-
Get info about the
<package>(direct or transient/sub-depedency)-
yarn audit | grep <package>- to check how many of the dependencies/sub-dependencies affected by the<package>) -
yarn why <package>- to check which dependencies and transient dependencies uses the <package> and which hoisted versions of the<package>so that it is easy to evaluate selective dependency resolution is possible when that is the only option
-
-
ncu -u <package>, examplencu -u ‘/^webpack*$/’will bump the version of packages starts with webpack in package.json (will not automatically install the packages) -
yarn(to install the updated package) -
yarn upgrade <package>will fix updated package’s dependencies and transient dependencies inyarn.lockto latest w.r.t version range specified inpackage.json(refer other useful comments for how to upgrade package groups) -
Fix breaking changes in the dependency you upgraded (most likely if you bump major version)
-
evaluate if selective dependency resolution is needed ->
yarn auditstill complains -
WARNING:
yarn upgradealso possible but commit the changes until step 5 before you try this beast (it may break most likely when the packages haven’t been upgraded for long time)
You can repeat this steps package by package
Greedy strategy(suitable for projects with less dependencies and for projects with 100% coverage):
1. ncu -u
2. yarn
3. yarn upgrade
4. evaluate if selective dependency resolution is needed -> `yarn audit` still complains
5. Fix breaking changes (builder: webpack, test: jest, lint: eslint, etc.,)** - yarn upgrade or yarn upgrade <package> is the key that it re-creates yarn.lock with latest deps and transient deps w.r.t version range specified in package.json
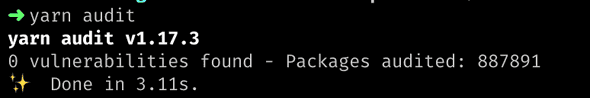
Fig.4. yarn audit 😊
Other useful comments:
yarn upgrade —pattern <glob>, will upgrade all the packages that matches the <glob>
yarn upgrade —scope <scope>, will upgrade all the scoped packages @scope
